To easily get into this topic. Let’s start with a simple question. What day-to-day devices do you think make up a network?
Simply, a group of electronics that connects to your LAN (local area network) and exchanges information to other devices spanning over other networks are what makes up a network. Data exchanged over the network could be over wireless (Wi-Fi) or wired communication. This varies based on the device communication capabilities. However transmitted data is useless unless processed. That’s where network components come in the picture. These components are designed to receive this data (either in the form of frames or packets), read the header and based on the destination address forwards or route it to the destination. For the scope of this article, we will only dive in the types of network components rather than routing and switching.
At home you have your telecom box that feeds your household with internet for your family and generally that would be more than enough. Unless your brother in the next room starts uploading huge documents and you’re playing an online game. I know this happens all the time. But generally these speeds would be enough. However, in larger companies you wouldn’t be able to maintain 500 employees over a telecom box. So these network components which are beefier in specs are deployed in cooled, highly secured rooms. In medium to large sized companies we typically find these network components: switches, routes, access-points, servers, endpoints, PoE (power over Ethernet), firewalls and IPS (intrusion prevention system) and controllers.
Let’s start with the first component which is a switch. There are two types of switches. Layer 2 or layer 3. A switch’s most basic function is firstly to connect all endpoints and to forward packets or frames from one source to a destination endpoint. Let’s visualize this a bit. Tim is sending a document from his PC (a personal computer/workstation is considered as an endpoint) to Alice’s workstation. Let’s not get into the intricate detail of how Tim is going to send the document but regardless of the protocol used, Tim’s PC needs to communicate with Alice’s PC. Once the document is sent over the network, the switch which connects these endpoints located in the same department, receives this data with the source from Tim’s PC and the destination to where this document needs to reach. In this case the destination is Alice’s PC.
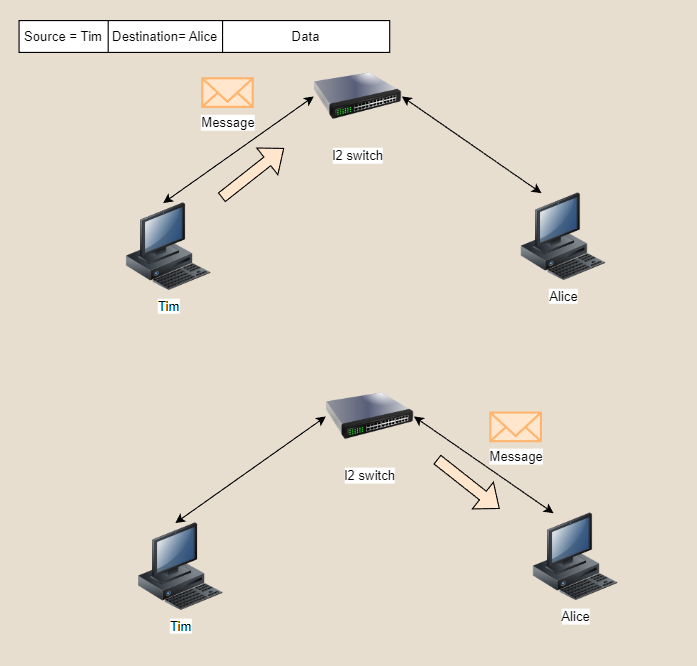
A L2 and L3 switch both forward data but it’s how they interpret data that differs. An L2 switch receives data in the form of frames. The simplest form of data in networking and when reading a frame it contains the source and MAC address. L3 on the other hand receives data in the form of packets which have the source and destination IP addresses in the header in addition to the MAC addresses. These switches are capable of routing packets over the network to endpoints which are not directly connected to the switch. Generally you deploy an L2 switch closer to the endpoints while L3 switches closer to the network core (handles network traffic in between other switches). You could in certain setups connect endpoints to L3 switches it’s mostly based on the use case of the setup. There are switches that are both L2 and L3 and these are capable of forwarding and routing. But generally they are more expensive.
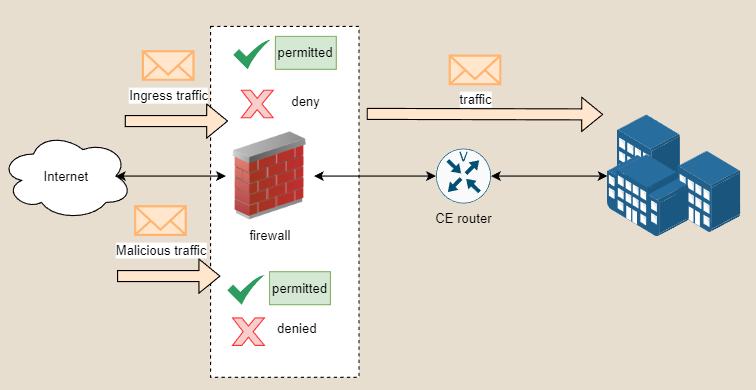
Routers handle only routing traffic which have a src IP to dest IP and are always found in the core part of the topology. While routers can handle outbound traffic to the internet it’s typically recommended to pair a router with a firewall. With a firewall you have an extra layer of protection and administrators can control which ingress traffic is permitted inside your company. Next generation firewalls are a better step of an improving in security as not only it has the features of a firewall, blocking and permitting based on IP and protocol but also now administrators have the capabilities to filter on application and location. In a big corporation, there is typically a security team who specifically administers firewalls. Not only firewalls but they sometimes have something called an IPS (intrusion prevention system). A system that detects and prevents cyber attacks based on patterns or traffic flows.
It’s always reassuring having a robust and redundant infrastructure as much as being able to scale. Office employees nowadays typically have several endpoints such as workstations or laptops, they have their own smartphones or they might bring an iPad if the company you work for has a BYOD (bring your own device) policy. Security cameras and department television all add up as endpoints so you must have enough ports on your switch for quick expansion. However not all endpoints require wired communication, some are purely wireless and that’s where access-points come in. These access-points operate somewhat similar to switches but instead of connecting devices through a cable, it connects wireless devices. Over a department you could span several access-points as you cover black spots (spots with low or weak signal) and over an entire building you might have tens or hundreds of access points (AP’s). You could configure each access point one-by-one or you could connect several access-points to a central controller. A WLC controller for instance would push generic configuration on connected AP’s and as an administrator it would benefit as to prevent mundane configuration, plus providing a central interface to manage all the AP’s. Each AP is connected through a wired connection to a switch. To reduce the extra power cable per AP, you could power each access point with the Ethernet cable if the switch supports PoE (power over Ethernet). With this rather than passing two cables (one for power and another for Ethernet) you need to pass only the Ethernet cable to the AP and it’s supplied with enough power.
Inside a network room it’s common to find servers. These servers are huge in storage, high on memory resources depending on their purpose. These are cooled as they overheat easily and are racked inside a network/server cabinet. You could host sensitive data or host the company software-housed applications for internal employees to access. Corporations are moving bit by bit away from servers to reduce upkeep costs and deploying everything on the cloud.
Conclusion
Devices all around us communicate over the network with the help of network components. There are L2 and L3 switches that provide forwarding and routing to connected endpoints over wired Ethernet cables. Routers that form part of the network core providing connectivity to external networks. These are secured with a firewall and IPS to detect and limit traffic to your company. There are access points that support wireless communication for wireless devices. Access points can be managed over WLC centralized controllers. We have PoE switches which are capable of powering AP’s with just one Ethernet cable. And finally servers that host data critical applications and IT services to local or external employees.






Leave a Reply